CVE-2023-1767 - Stored XSS on Snyk Advisor service can allow full fabrication of npm packages health score [𝕏]
09 Apr 2023Originally posted on X
Nothing too exciting about yet another stored #XSS on a public security service.
Question is however - what you do with it?
A story about a fresh new CVE in the packages advisory tool of @snyksec - only this time with a fun twist! 🧵
(full story on ) weizman.github.io/2023/04/10/sny…
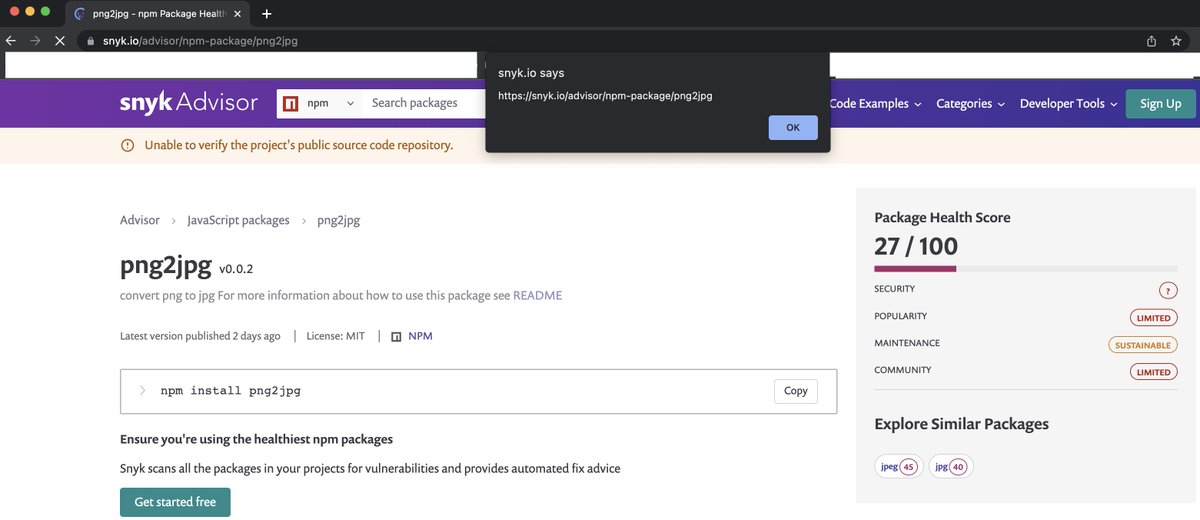
Last month I found a stored XSS on Snyk’s advisory tool. By accident.
I just wanted to have a look at an npm package I maintain, and that’s a service the advisory provides.
In case you’re not familiar with it, it’s a blessed initiative by the @snyksec folks.
https://snyk.io/advisor/
Its purpose is to give you the most accurate insights on how legit an npm (or a python) package is when considering to use it - insights you don’t get from npm itself.
I took a look at my package which naively contains in its README the string “<iframe>” and was surprised to see that instead of presenting it as-is, the advisor rendered the iframe!
Markdown-to-XSS isn’t a new technique actually (look it up), but hold on - the twist is coming!
What do you do with a stored XSS? You try to compromise logged-in users, right?
Not this time! We can go BIGGER!
We can turn the whole point of the advisory tool against itself 😈
I found a stackoverflow thread online of people looking for an npm package that turns pngs to jpgs.
I registered “png2jpg” (already deleted) as a legitimate converter tool, but instead of actually implementing such, index.js was basically “console.log(‘supply chain attack!!’)”
A day later, the adisory analyzed my package and granted it a terrible health score for being so new and not adopted.
Although that’s completely fair, it’s going to make it very hard to convince my victims to install my package.
Luckily, my Markdown-to-XSS can change that 😉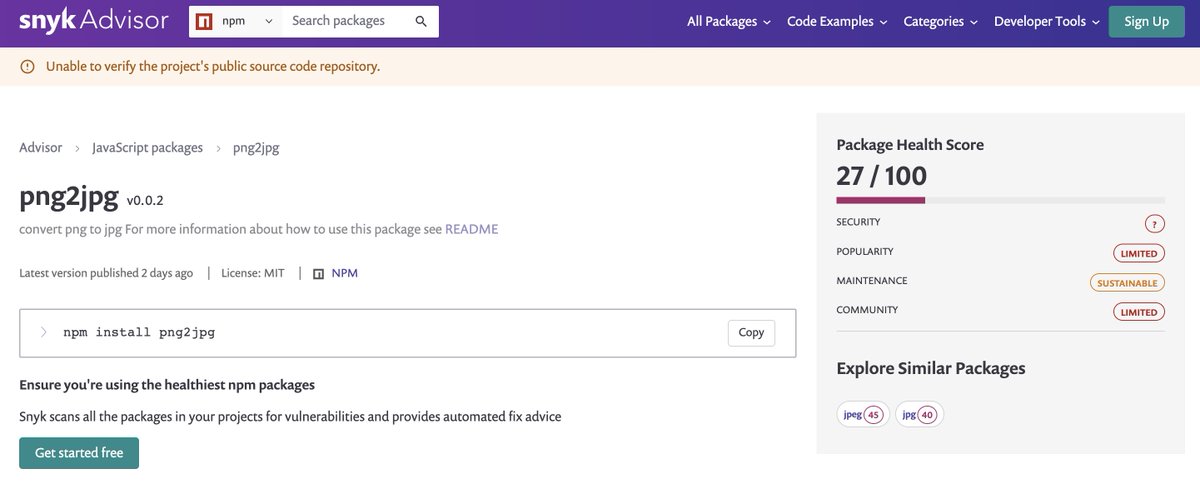
I published a new version to npm where I added
“<img src=1 onerror=‘alert(location.href)’>”
to the bottom of the README file, just to prove my XSS works: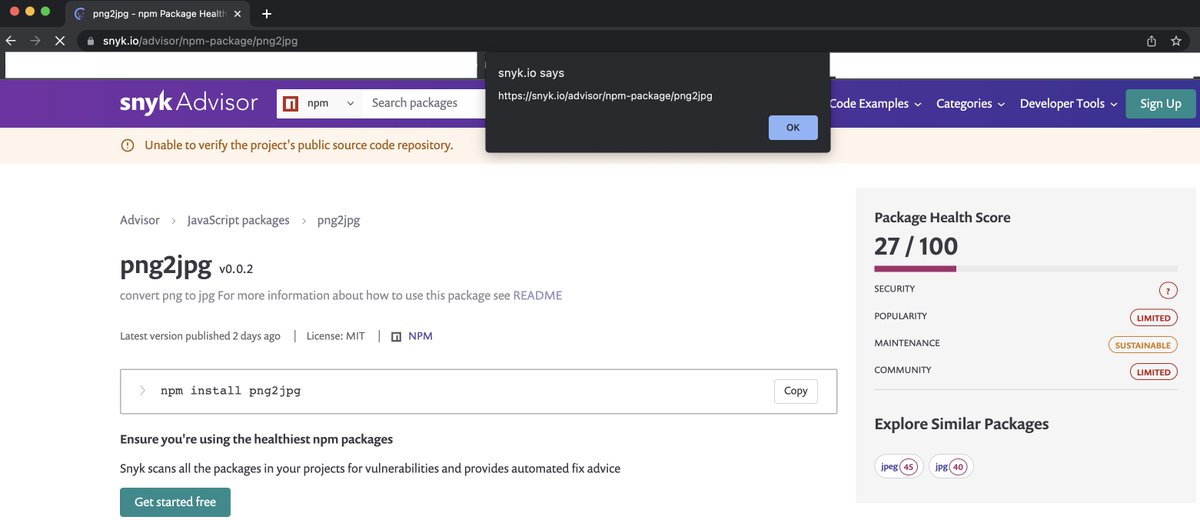
Finally, I uploaded the final version. This time I leveraged the XSS to change the layout in the advisory to lie about my package and present it as legitimate and highly popular!
And the result? Well, judge for yourself: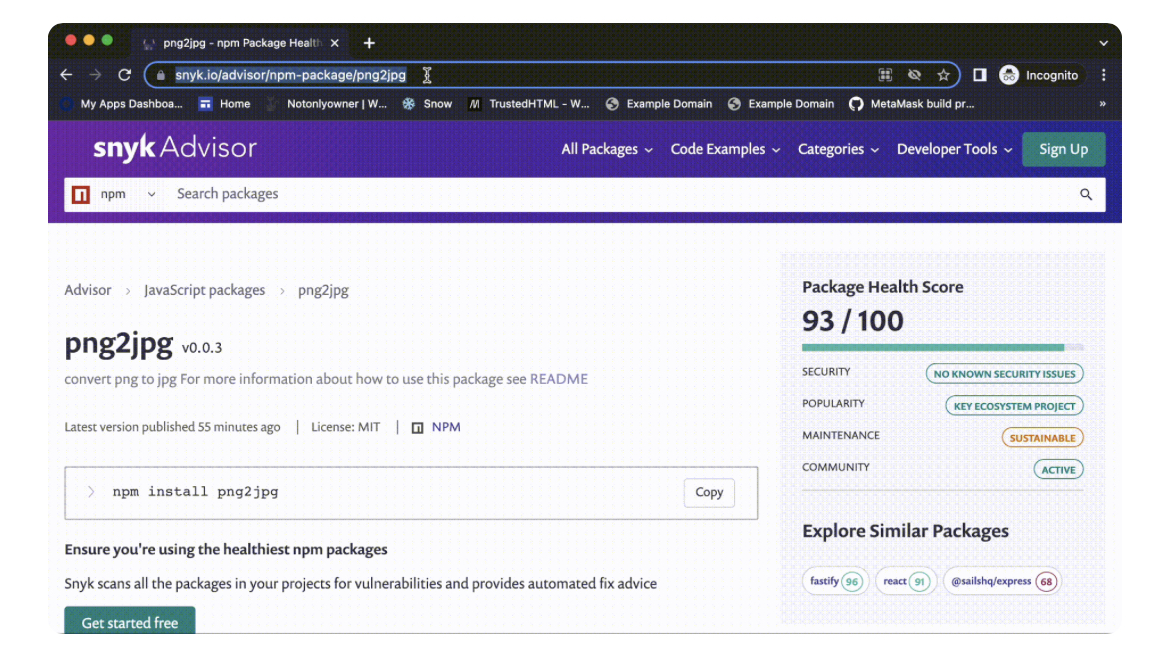
All is left is to post https://snyk.io/advisor/npm-package/png2jpg in the stackoverflow thread claiming this can convert your pngs - it looks to good to not use it!
People trust tools like the advisory to tell them if some packages are safe to use or not, because how else could they know? (Except for reviewing their code but come on)
That is why such a breach can potentially be just as dangerous - a single point of failure.
@snyksec were highly professional in the process of patching this. When creating similar services make sure (1) you’re aware of Markdown-to-XSS and (2) implement CSP protection.
Thanks @ace__pace for help with the post.
If you’re into javascript security follow me for more 😊
@snyksec @ace__pace
Question is however - what you do with it?
A story about a fresh new CVE in the packages advisory tool of @snyksec - only this time with a fun twist! 🧵
(full story on ) weizman.github.io/2023/04/10/sny…

Last month I found a stored XSS on Snyk’s advisory tool. By accident.
I just wanted to have a look at an npm package I maintain, and that’s a service the advisory provides.
In case you’re not familiar with it, it’s a blessed initiative by the @snyksec folks.
https://snyk.io/advisor/
Its purpose is to give you the most accurate insights on how legit an npm (or a python) package is when considering to use it - insights you don’t get from npm itself.
I took a look at my package which naively contains in its README the string “<iframe>” and was surprised to see that instead of presenting it as-is, the advisor rendered the iframe!
Markdown-to-XSS isn’t a new technique actually (look it up), but hold on - the twist is coming!
What do you do with a stored XSS? You try to compromise logged-in users, right?
Not this time! We can go BIGGER!
We can turn the whole point of the advisory tool against itself 😈
I found a stackoverflow thread online of people looking for an npm package that turns pngs to jpgs.
I registered “png2jpg” (already deleted) as a legitimate converter tool, but instead of actually implementing such, index.js was basically “console.log(‘supply chain attack!!’)”
A day later, the adisory analyzed my package and granted it a terrible health score for being so new and not adopted.
Although that’s completely fair, it’s going to make it very hard to convince my victims to install my package.
Luckily, my Markdown-to-XSS can change that 😉

I published a new version to npm where I added
“<img src=1 onerror=‘alert(location.href)’>”
to the bottom of the README file, just to prove my XSS works:

Finally, I uploaded the final version. This time I leveraged the XSS to change the layout in the advisory to lie about my package and present it as legitimate and highly popular!
And the result? Well, judge for yourself:

All is left is to post https://snyk.io/advisor/npm-package/png2jpg in the stackoverflow thread claiming this can convert your pngs - it looks to good to not use it!
People trust tools like the advisory to tell them if some packages are safe to use or not, because how else could they know? (Except for reviewing their code but come on)
That is why such a breach can potentially be just as dangerous - a single point of failure.
@snyksec were highly professional in the process of patching this. When creating similar services make sure (1) you’re aware of Markdown-to-XSS and (2) implement CSP protection.
Thanks @ace__pace for help with the post.
If you’re into javascript security follow me for more 😊
@snyksec @ace__pace